Be on the Lookout: Impact of SolarWinds Orion Compromise on Cloud-Based Solutions
by Alicia Lynch Vice President, Chief Information Security Officer at SAIC, MBA, CISSP
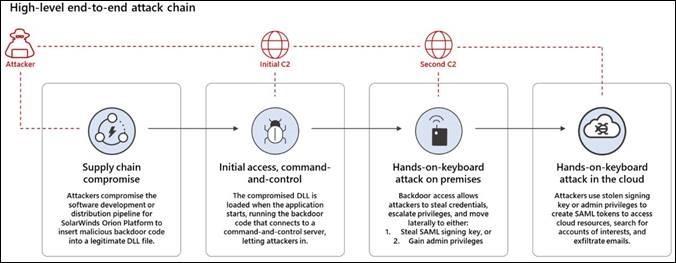
This is an update to the FireEye and SolarWinds messages I posted on Dec. 9, Dec. 19, and Jan. 12. This message contains additional information.
As the fallout from the SolarWinds Orion platform hack continues, experts have confirmed that the attack targeted specific API keys from Microsoft Azure and Amazon Web Services (AWS). If an attacker were able to extract these keys from any Orion databases compromised by the SUNBURST malware, they could decrypt the keys and subsequently gain access to the victim’s cloud-based services.
Note: Orion software that is deployed in AWS or Azure environments may use root API keys that would give attackers comprehensive administrative privileges for compromised accounts.
SUNBURST Malware Can Access Cloud Environments
Orion databases may store AWS and Azure API keys, which would enable an attacker exploiting Orion with the SUNBURST malware to take over and compromise these accounts. If deployed on AWS or Azure, Orion may also have access to root API keys. These keys can enable an attacker to have full admin privileges to the account that Orion is deployed on.
What countermeasures are recommended for my organization’s cybersecurity team?
It is recommended that your organization’s cybersecurity team take the following actions for any instances of SolarWinds Orion in cloud-based infrastructure:
- Consider everything Orion touches as compromised. If your instance was not deployed on an account completely separate from your environment, compromised resources and identities may still be connected to the cloud.
- Conduct a manual review of each identity and resource to determine the extent of exposure if Orion was not deployed on a standalone account.
- Treat the Orion IAM identity in your cloud environment as compromised as well.
- Identify all potentially exposed credentials and rotate them immediately.
- Evaluate your deployment to ensure that you are practicing least privilege, limiting access to only what is necessary to operate.
- Ensure you are running the updated and patched versions of Orion applicable to your instance:
2019.4 HF 6 (released December 14, 2020)
2020.2.1 HF 2 (released December 15, 2020)
2019.2 SUPERNOVA Patch (released December 23, 2020)
2018.4 SUPERNOVA Patch (released December 23, 2020)
2018.2 SUPERNOVA Patch (released December 23, 2020)
Stay Vigilant
Continue to work with your organization to ensure they have implemented the countermeasures described above.

